One Identity, One Experience:
How I unified login, multi-factor authentication, and user profile experiences post-acquisition
Users shouldn’t have to learn the same thing twice.
Post-acquisition, EROAD and Coretex users navigated two enterprise platforms with different logins, profiles, and rules. Using both meant repeated effort, frustration, and duplicated work.
There was no MFA, no shared identity, and no consistent experience. Teams were building the same features twice, adding security risk and complexity.
As part of unifying the platforms, I led the design of a shared identity system, spanning login, MFA, and user profiles, built once, deployed across both products.
Through journey mapping, research, and close collaboration with security, product, and engineering, I aligned two separate experiences into one cohesive system. The result: faster, low-friction sign-ins, enterprise-grade security, fewer support issues, and a scalable identity foundation.
Overview
Responsibilities
UX research, End-to-end journey mapping, Identity system design, MFA & security flows, Systems thinking, Post-acquisition experience unification
Role & Team
Lead UX designer (my role)
Engineers
Architecture
Product manager
Security specialist
Timeline
3 months
Due to NDA restrictions, only limited and low-fidelity design visuals are shown
Business Impact
↓ 28% reduction in authentication-related support tickets
↑ 40% MFA adoption within the first rollout phase
For the business, I unified identity across two live platforms, cutting duplicated development, strengthening security, improving UX, and future-proofing the platform.
Context & challenge
The post-acquisition reality
After the acquisition, the company now supported two large enterprise SaaS platforms solving similar user needs.
Both platforms remained live
Both had overlapping users
Both handled identity differently
There was no MFA, no shared login experience, and no consistent mental model. Users moving between products faced friction, while internal teams were duplicating work and increasing security risk.
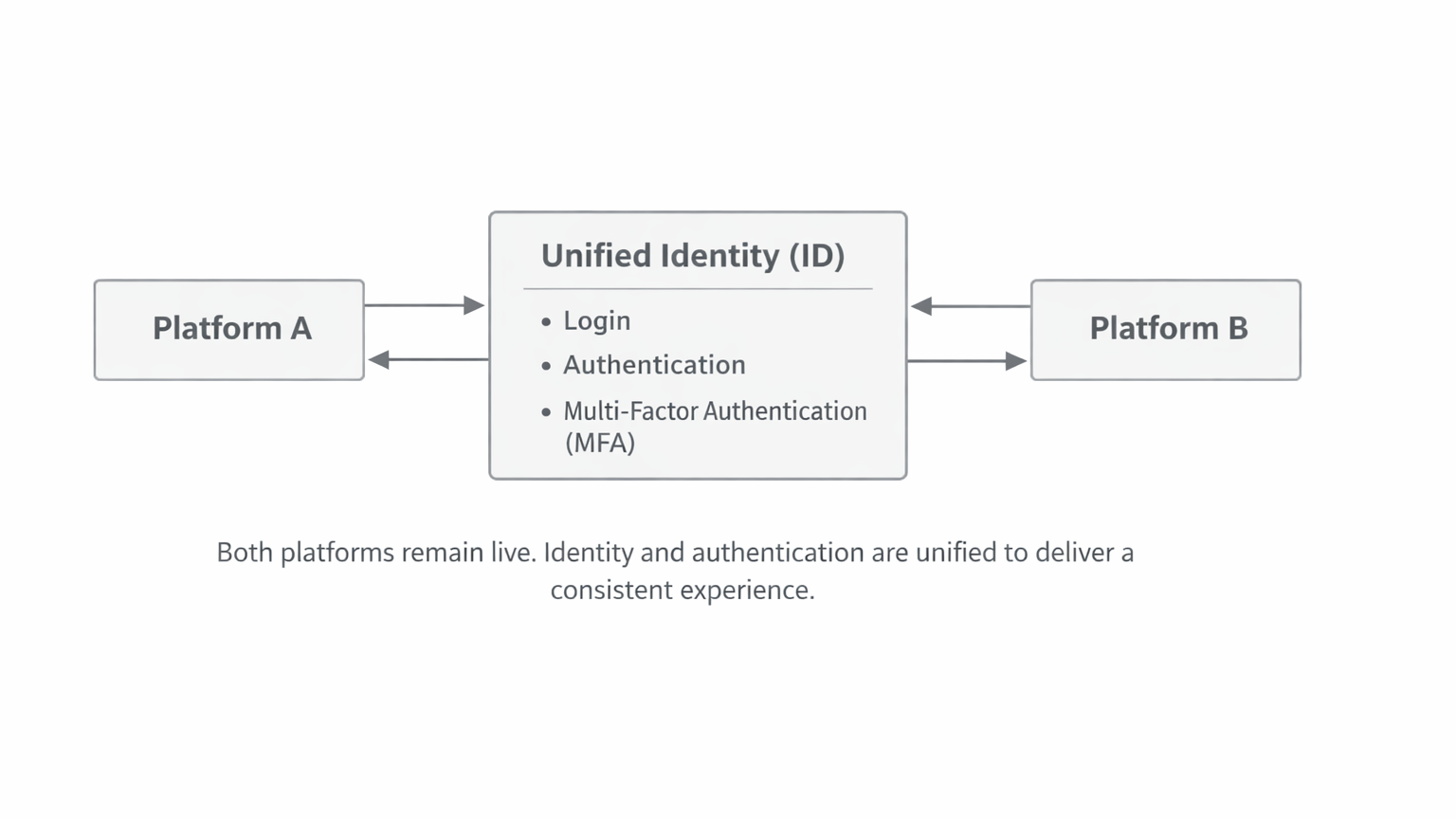
This project focused on unifying the experience, not the platforms themselves.
Empathy
What users were actually trying to do
Users weren’t thinking about “authentication systems.”
They were:
Logging in quickly during busy workdays
Switching between platforms mid-task
Supporting teams with different access levels
Recovering access when something went wrong
Inconsistencies slowed them down and, more importantly, eroded confidence — especially in moments of failure or recovery. This became the lens for every design decision.
Current state analysis
Understanding two systems before changing one
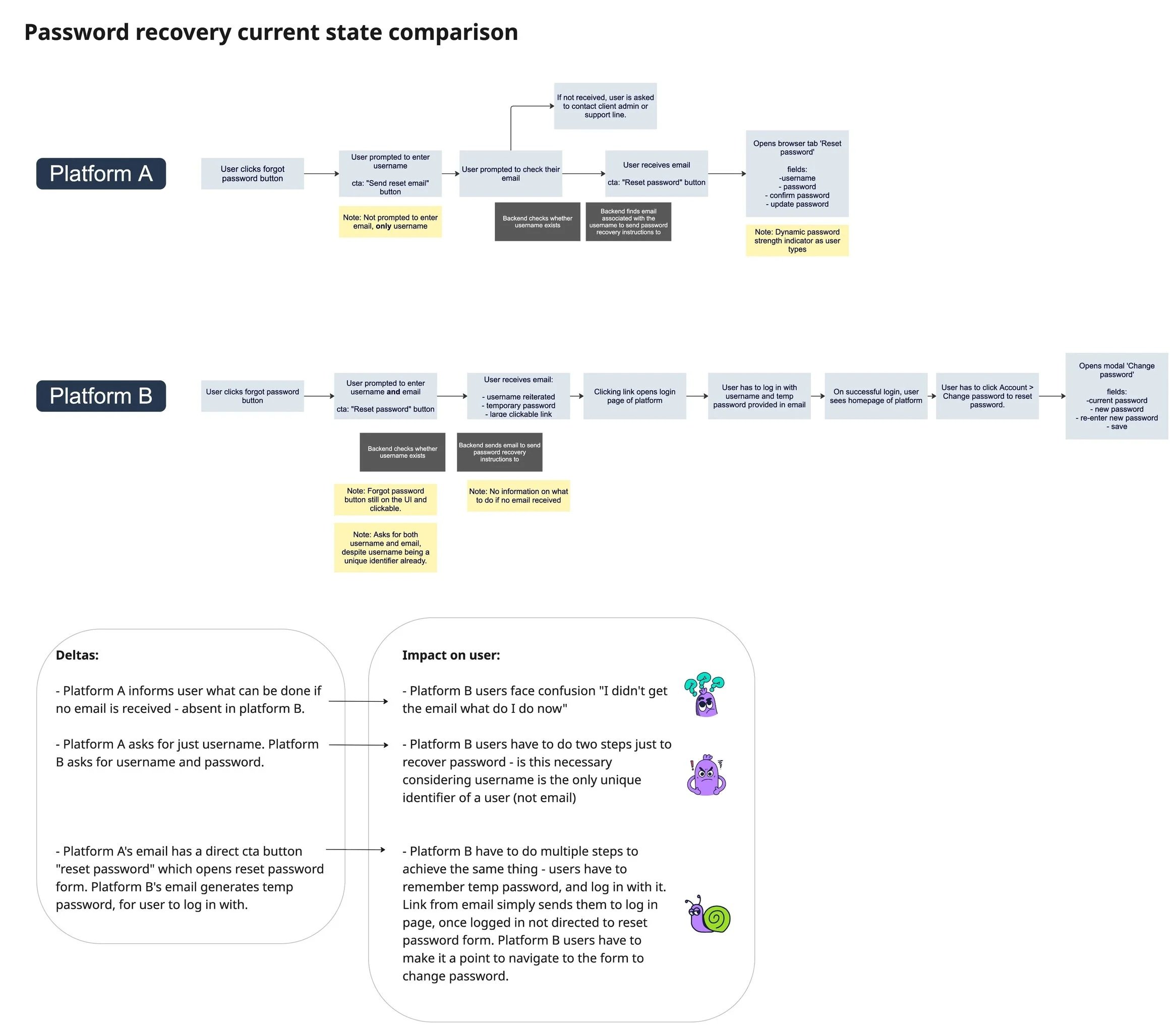
Before designing anything, I needed to understand the full identity surface area across both platforms.
I mapped:
Login and authentication flows
Success, failure, and recovery states
Where profile and security settings lived
Role-based visibility and permissions
Differences in rules, language, and patterns
This work surfaced clear opportunities for consolidation — while also revealing technical and product constraints that shaped what could realistically be unified.
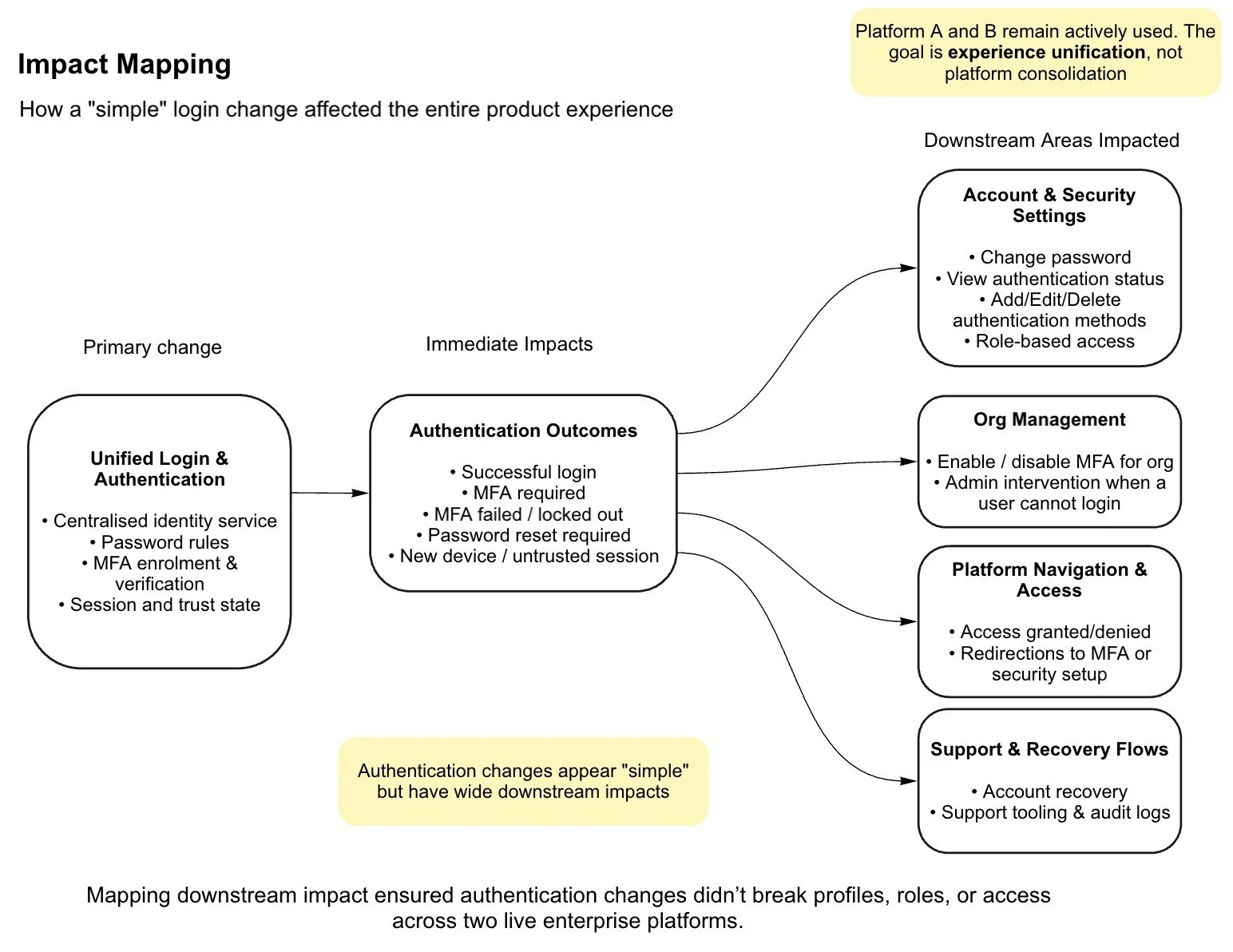
Sytems thinking & Impact mapping
Authentication doesn’t end at sign-in
Authentication wasn’t just a front-door problem.
Introducing MFA and unifying authentication meant users also needed:
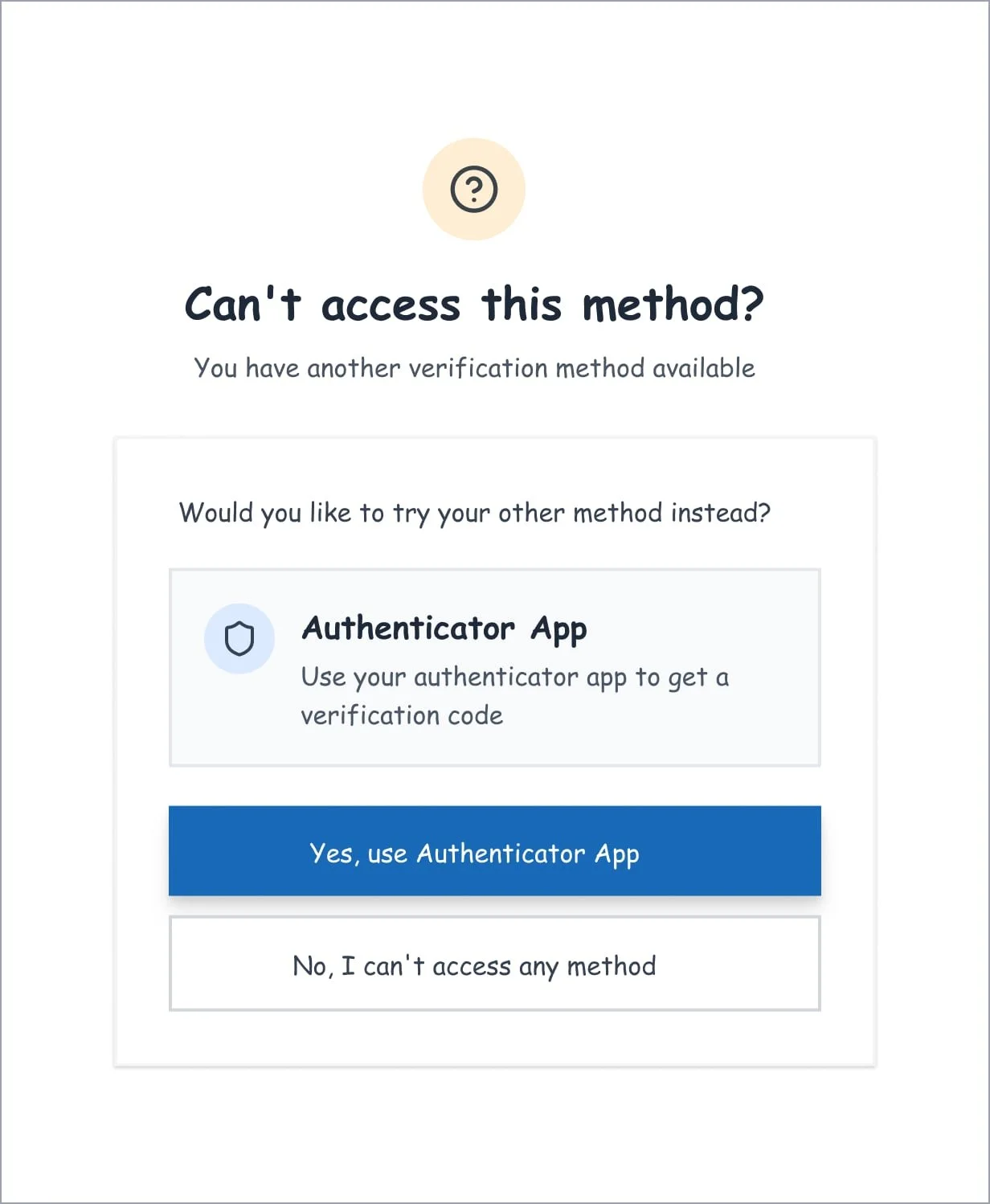
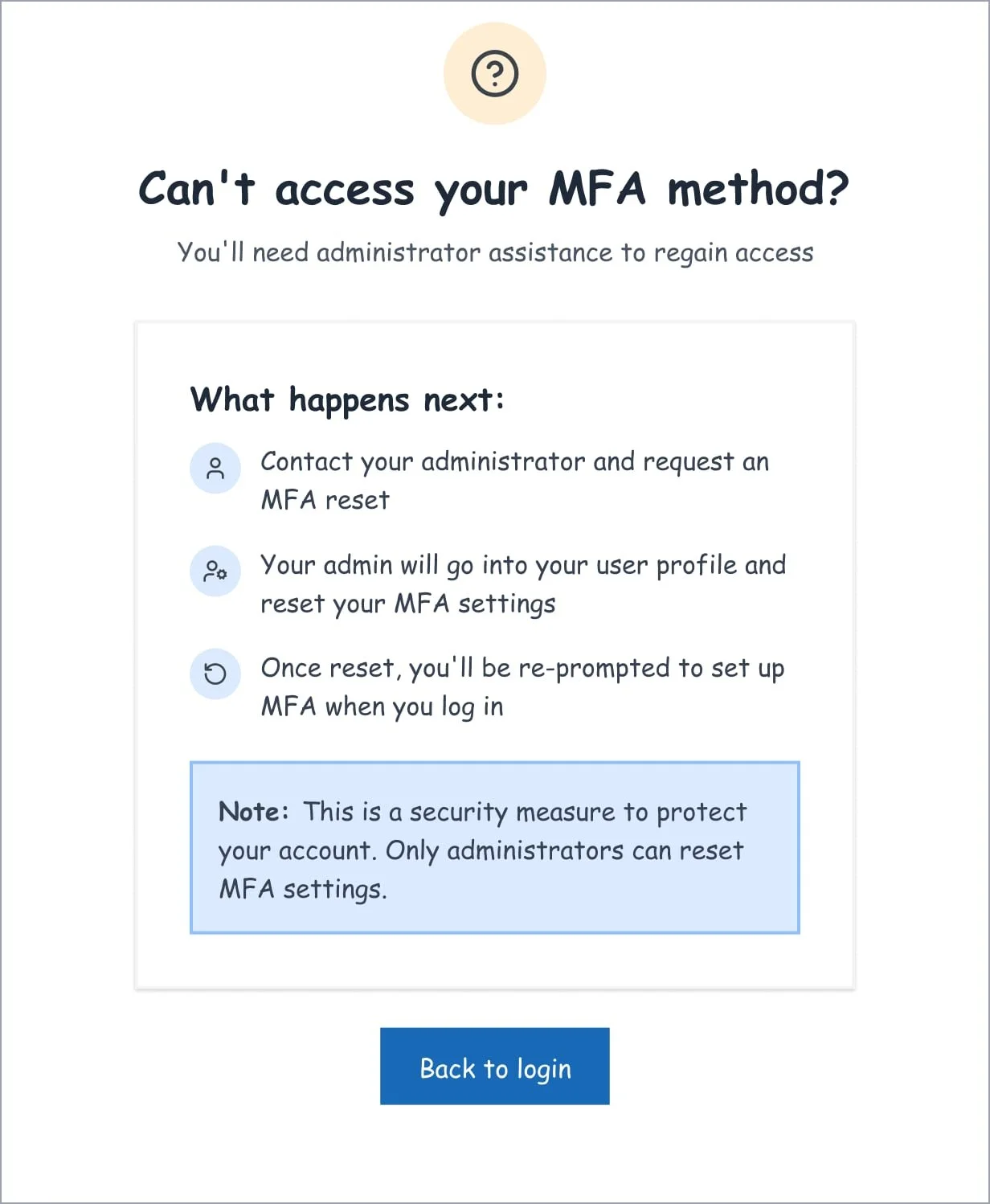
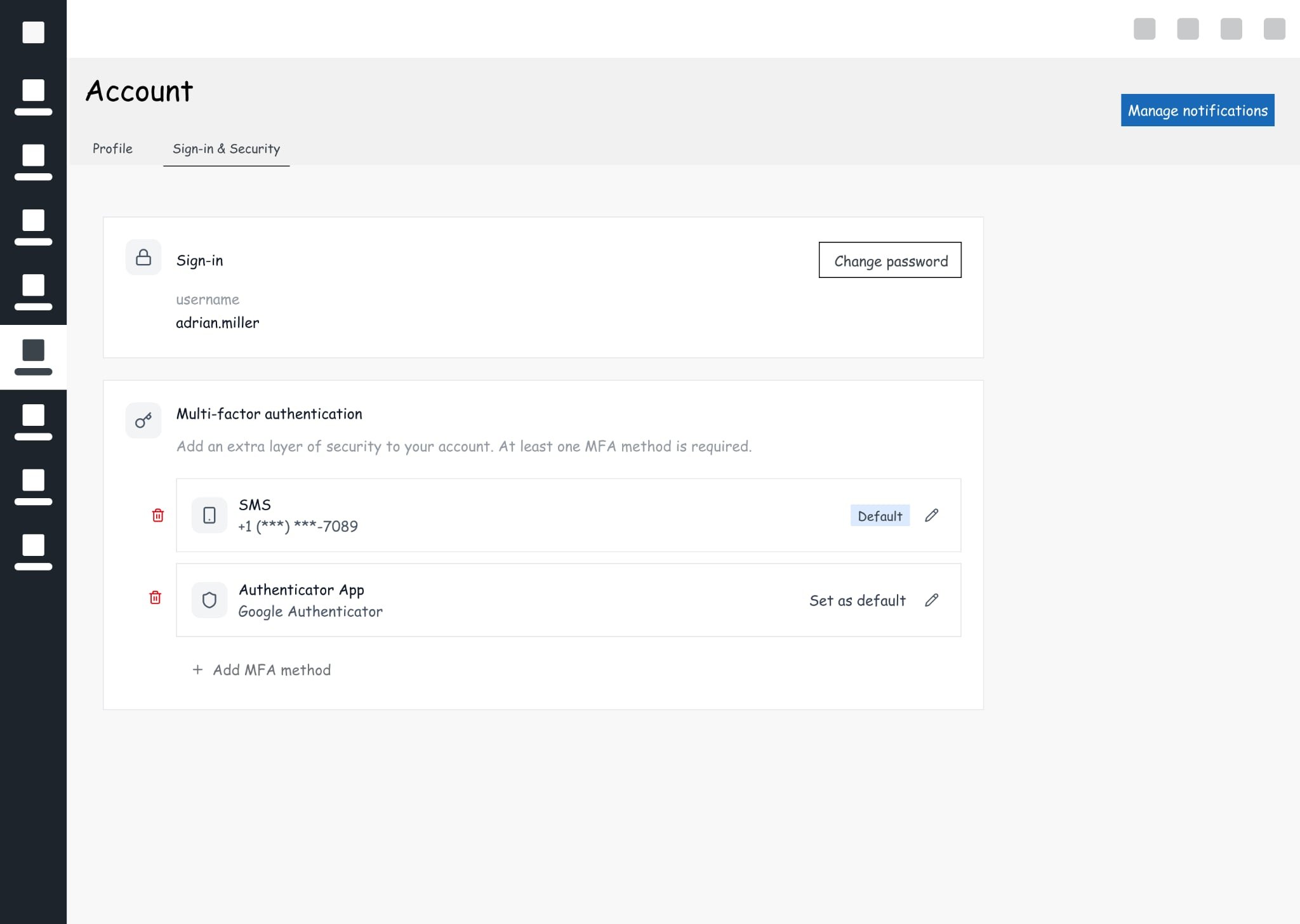
Clear ways to manage passwords and MFA
Predictable recovery when things failed
Security settings that felt connected, not scattered
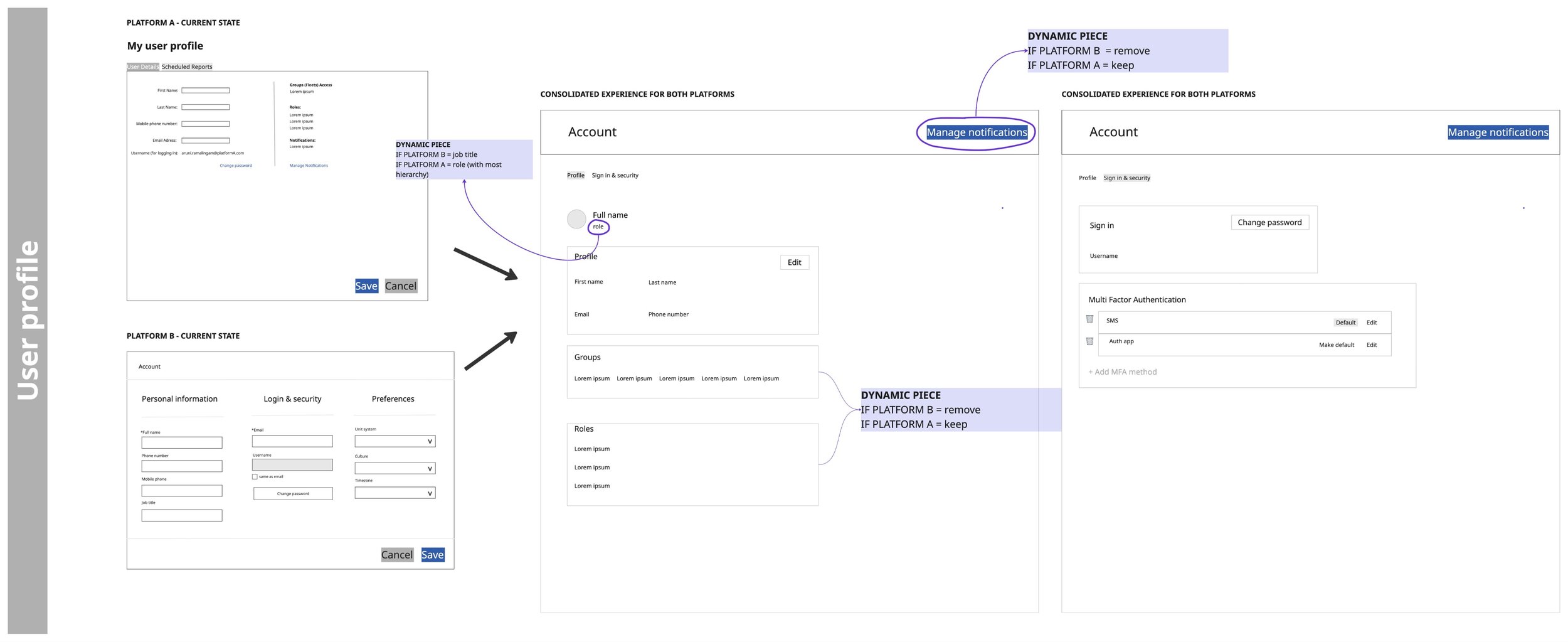
Even though profile management remained decentralised within each product, it was still part of the identity experience and had to feel coherent across both platforms.
At the system level, I mapped every surface affected by these changes: from profiles and security settings to roles, navigation, and recovery flows. This ensured we could unify the experience without breaking access, permissions, or trust across Platform A and Platform B.
User journey map
Designing for the moments users feel most vulnerable
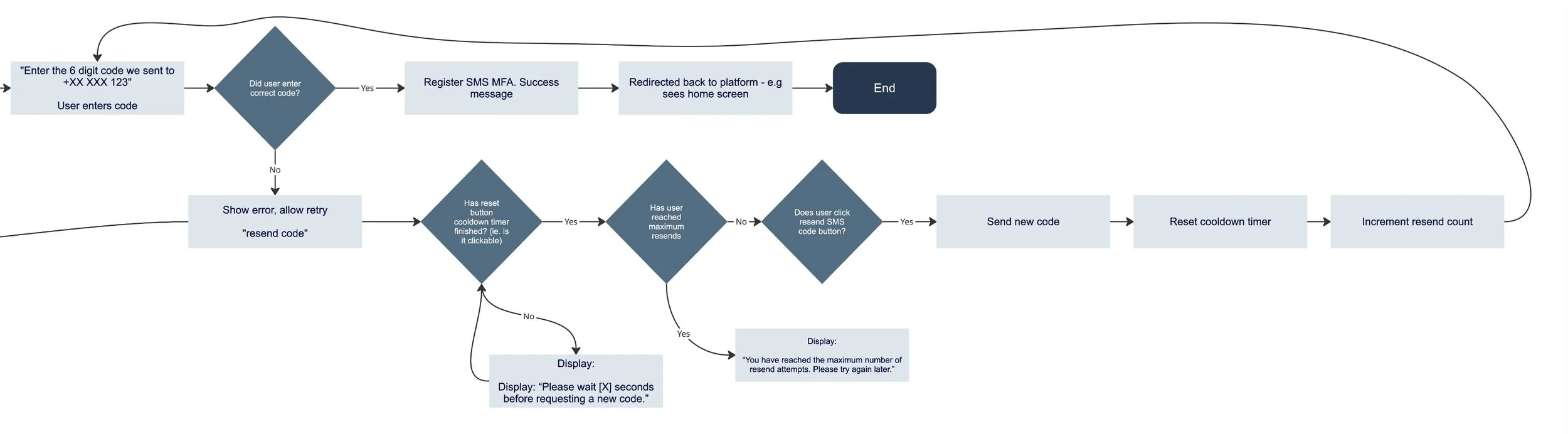
Failed MFA attempts
Lockouts under time pressure
Urgent access recovery needs
Managing security without technical knowledge
By designing with these moments in mind, we reduced anxiety and confusion instead of introducing new points of failure. The combined view of system and human impact helped create an authentication experience that is secure, coherent, and user-friendly across both platforms.
At the human level, I identified the moments where authentication failures are most stressful:
Experience consolidation
One mental model, two platforms
Using the insights from current-state analysis, I designed a single identity experience flexible enough to support both platforms.
Design principles:
One clear mental model, regardless of product
Security that’s visible but not intimidating
Consistency without forcing identical UIs
Designed once, reusable across products
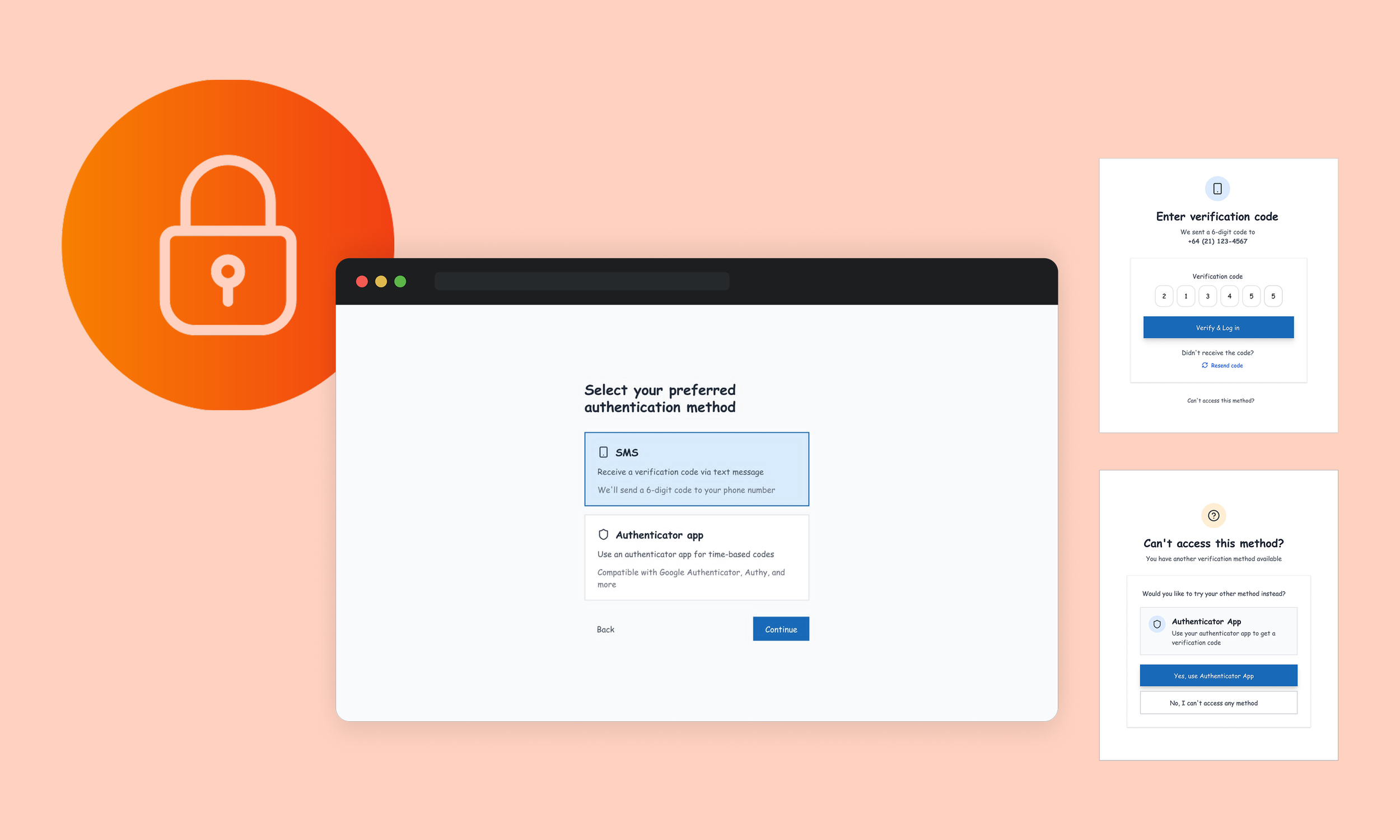
Low-fidelity concepts aligned teams early, followed by high-fidelity designs that respected each platform’s constraints while delivering a unified experience.
Security by design
Enterprise-grade security, human-centred UX
MFA was designed as a core part of the identity system — not an afterthought.
I designed:
MFA enrolment and recovery flows
Clear system feedback and error handling
Guardrails aligned with security standards
User-friendly explanations for non-technical users
The focus was on protecting users without punishing mistakes.
Design iterations
Validating the designs
Validation was conducted through a combination of usability testing, stakeholder alignment, and technical review to de-risk the MFA rollout across both products.
For this project, I specifically engaged the Customer Success and Support teamsto validate real-world scenarios and edge cases informed by customer issues.
Insights from testing informed rapid iterations, ensuring the final solution strengthened account security while maintaining a seamless, low-friction user experience.
Outcome
A shared identity foundation, built to scale
The final solution delivered:
A unified login experience across both platforms
Enterprise-grade MFA with clear management paths
Reduced friction for users moving between products
A scalable identity system for future growth
Most importantly, users no longer had to relearn how to access or secure their account just because they were using a different product.
Identity as a System, Not a Flow
Reflection
This project reinforced the importance of stepping back and looking across the entire identity landscape, not just individual flows. Deeply understanding the current state and the downstream impact of something as seemingly simple as login was a major factor in the project’s success.
Designing within complex, live platforms required restraint, empathy, and a clear point of view. Much of the impact came from removing the friction users had quietly learned to work around.
Theres More to Share!
There’s more depth behind the flows, interaction decisions, mobile optimisations and usability tests. I’m happy to share these in interviews or private walkthroughs.